A computer network is more than just cables and routers—it's the foundation of every company's IT infrastructure. In enterprise environments, the network connects not only computers but entire clusters, microservices, data storage, IoT devices, and security systems. It enables business applications to communicate, backups to run, CI/CD to function, and remote services to be accessible. Understanding what a computer network is in this context is not theory, but practical knowledge that allows for the design of fault-tolerant and scalable solutions.


A Computer Network Is Not Just a Cable and an IP Address—How to Understand Its Role in Modern IT
In enterprise environments, the concept of a computer network means much more than connectivity between devices. It is the backbone of the IT infrastructure, supporting communication between services, access to applications, permission control, and security monitoring. The structure of a computer network in server rooms includes not only physical cables and network devices but also logical layers—VLANs, segmentation, protocols and routing rules, as well as resource management through SDN. The network no longer acts merely as a passive transmission channel—it is a dynamic, actively managed system that affects whether applications scale smoothly and whether ERP, CRM, or data warehouse systems perform as expected.
Understanding the network as a service environment is crucial today. Increasingly, you are dealing with hybrid topologies, where a wide area computer network connects local resources with cloud services—and everything must work as a single, coherent organism. Therefore, when planning a modern environment, you cannot limit yourself to physical components. You must consider routing between logical subnets, access control, route redundancy, support for overlay/underlay, and integration with automation systems. Without this, no CI/CD, backup, or disaster recovery will be reliable.
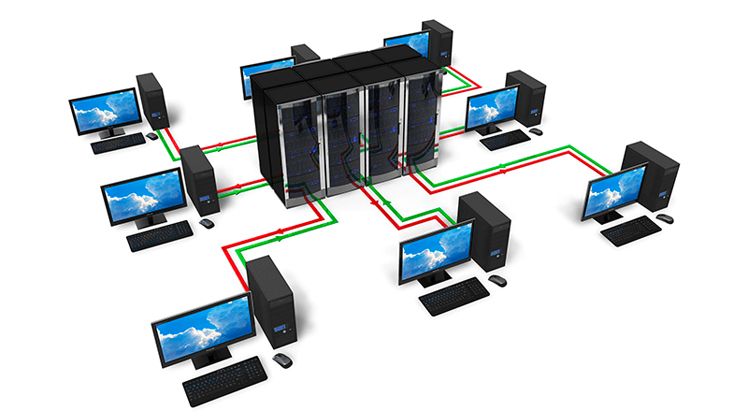

Client-Server, Peer-to-Peer, and the Rest—Architectures You Need to Differentiate
In enterprise-class networks, the client-server model still dominates, where resources—applications, data, services—are located on a central server, and end devices access them remotely. This model allows for full control over traffic, access, and resources, but it requires a well-designed architecture—both hardware and logical. This solution helps minimize the risk of data breaches, streamline user management, and implement computer network security policies.
However, it's important to remember that any failure on the central server's side results in the unavailability of the entire service.
On the other hand, we have the peer-to-peer architecture, which is no longer common in production environments but can be useful in testing, simulations, or where devices need to exchange data locally without central management. Knowing both models and being able to distinguish between them when designing a network is a key competency if you want to avoid design errors. Building a computer network should start with choosing a logical architecture, and only then should you move on to planning routing, addressing, switches, or QoS classes. Without this, any investment in hardware will be just an expensive collection of devices without cohesion.
What Makes Up a Modern Computer Network? Not Just a Router and a Switch
When talking about the elements of computer networks in a server environment, at least five main layers must be distinguished:
- End devices (e.g., servers, workstations, IoT devices),
- Network devices (routers, switches, access points),
- Transmission media (fiber optics, twisted-pair cables, radio links),
- Communication protocols and management software.
Today, just as important as the RJ-45 port is controlling who can use that port and when, with what bandwidth, and to which resources they have access. Without intelligent management of this traffic, even the best hardware won't solve basic security or performance problems.
In a modern data center, it's not enough to buy "good hardware." You need integration with traffic monitoring tools (e.g., NetFlow, Zabbix), network segmentation (VLAN, micro-segmentation), connection redundancy, and support for dynamic protocols (OSPF, BGP). Added to this is the increasingly popular management of the network layer through software—SDN (Software-Defined Networking). This allows you to react automatically to overloads, change packet routes without restarting services, and create logical networks independent of physical cabling.
Segmentation and Computer Network Security—When Is a Subnet Not Enough?
If you have been dividing your network solely based on physical IP subnets until now, it's time for a change. Modern production environments require segmentation at the VLAN level, micro-segmentation, and traffic policies that allow you to block, limit, and track packets between different infrastructure elements. Computer network security cannot rely solely on a firewall at the edge. It involves policies in switches, ACL rules, trunk/access port separation, as well as application-level control.
Logical segmentation not only improves security but also performance—it reduces broadcast traffic, improves manageability, and allows for the implementation of QoS rules per group. For large companies using ERP, CRM, HR systems, and a host of SaaS tools, this is the only way to maintain order and service speed. Micro-segmentation, for example, allows you to isolate the accounting application from the internet without shutting down the entire network. In practice, this means fewer instances of lateral movement in the event of an attack and a faster response.
Cloud, SDN, Overlay—A Modern Computer Network That Keeps Up with Scaling
Today's enterprise computer network must be dynamic, flexible, and ready to scale—one that can seamlessly connect physical servers in a local data center with resources in AWS, Azure, or GCP. This is where solutions like overlay/underlay, SDN, micro-segmentation, and Network as a Service come in. Each of these elements allows you to manage the network so that you don't have to re-cable every time the environment's topology changes. SDN allows for central management of routing and access rules, while an overlay lets you create logical networks over the physical infrastructure without having to disrupt its structure.
Increasingly, companies are implementing the NaaS (Network as a Service) model—where a cloud operator provides ready-made solutions: VPN, load balancing, firewalls, segmentation, and traffic policies. This allows you to expand your IT environment without investing in more switches or rack cabinets. What's more, you get access to advanced monitoring, encryption, traffic logging, and compliance with standards like GDPR or ISO. As a result, even smaller companies can benefit from an architecture that just 5 years ago was reserved for banks. If your network can't keep up with the pace of application development, it's time to redefine it. Because today, it's not applications that adapt to the infrastructure—it's the infrastructure that must keep up with the applications.

































