For many administrators, SNMP is associated with "something that collects data from routers." But before you set up your first agent and connect your monitoring system, it's worth understanding how this protocol works, what to expect from it—and what you absolutely should not do. Because while SNMP can be a priceless source of information about your network, it can also easily be turned into a source of problems. In this post, we'll show you how to approach the topic wisely—from versions and security, through architecture, to the traps you can fall into right at the implementation stage.


What is SNMP and Why is it Worth Knowing Before Implementation?
The Simple Network Management Protocol is a way to know what's happening with your network—before users start calling to say "something isn't working." If you're wondering what SNMP is in practice, the answer is simple: it's a mechanism that allows you to read and modify the state of network devices - routers, switches, servers, UPSs, and even printers—from a single location. You don't have to log into each device separately to check the temperature, port utilization, or the number of interface errors. All you need is a configured SNMP agent and the right OIDs, and everything flows into your console.
But SNMP isn't just about monitoring. Properly configured SNMP management can also allow you to perform "Set" operations - that is, remotely changing parameters. In theory, you could even disable a port or set traffic priority via SNMP. Is this used in daily work? Rarely—because it requires caution and complete trust in the configuration. But it's worth knowing that the SNMP protocol is not limited to reading; it also has administrative functions. And before you implement it in a production environment, you must be aware of what you are opening up—and what needs to be secured.

SNMP Formats – Which One Makes Sense Today?
On paper, everything looks similar- every version of SNMP can send a query, receive a response, and listen for traps. But the differences begin where security and integration with corporate systems come into play.
- SNMPv1 is the absolute minimum - it sends data in plain text, encrypts nothing, and doesn't allow for extensive access rules. Today, however, it should not be used in any production environment, not even a closed one.
- SNMPv2c is a step forward - it offers a few more capabilities and better performance, but still has the same problem: a lack of authorization and encryption.
- It's SNMPv3 that brings specifics: authentication using MD5/SHA, data encryption (e.g., via AES), and access control at the user and IP address level. If you care about your SNMP management not opening a hole in your infrastructure, this is the version that should be the basis of your implementation. Interestingly, SNMPv3 also supports the TSM model, which means tunneling over TLS/DTLS- and that's a whole different league when it comes to compliance with security policies.
In short: SNMPv3 is the only reasonable option today - and everything else is a half-measure.
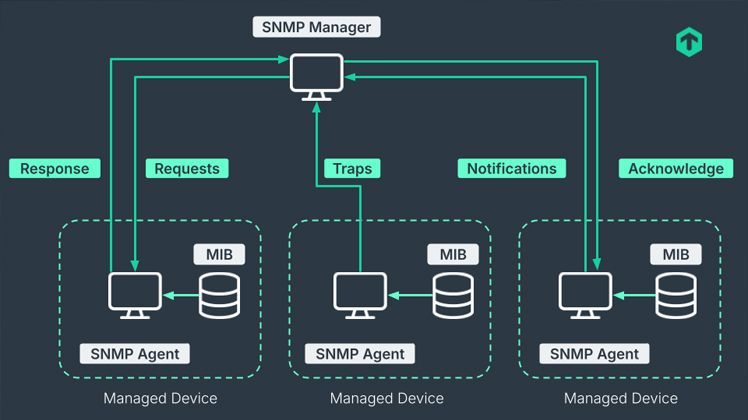
Agent, MIB, OID… or How SNMP Really Works "Under the Hood"
At first glance, SNMP seems simple - but if you're planning a real-world implementation, you need to understand the underlying architecture of the protocol. Everything is based on three pillars:
- Agents, which "live" on devices and respond to queries.
- MIBs (Management Information Bases), which are databases organized in a tree structure.
- OIDs (Object Identifiers), which are nothing more than unique addresses for specific pieces of information. Every interface, every CPU, every statistic has its own OID—and this is what the SNMP agent uses.
From an administrator's point of view, the most important thing is to skillfully design the MIB—that is, to choose what is actually worth monitoring.
- If you collect everything, you'll flood your NMS (Network Management System) with unnecessary data.
- If you collect too little, you'll miss a failure.
The best approach? Your own custom MIB, tailored to your specific infrastructure. Standard MIBs cover a lot, but private ones—created by hardware manufacturers like Cisco, HPE, or Dell—are also useful. Thanks to them, you can monitor things not available in the basic trees, like memory ECC errors, RAID status, or the battery level in an uninterruptible power supply.
SNMP in Practice – How Not to Crash Your Network During Implementation?
Theoretically, SNMP is just about reading data - but in practice, poorly configured agents can cause quite a bit of chaos.
The most common mistake? An overly aggressive data collection schedule or "GetBulk" queries that overload the device. It also happens that poorly configured traps spam the management server with hundreds of useless notifications, causing administrators to ignore alerts - even critical ones.
The second problem is a lack of testing. Before you launch the full configuration in a production environment, test SNMP on a trial group of devices. snmpwalk, snmpget, and snmptrapd are tools you should be familiar with from day one.
Implementing SNMP doesn't end with starting the agent. You need to prepare an SNMP management policy that defines not only the scope of the data being collected but also who has access, what the password rotation policy looks like, and whether unauthorized query attempts are logged. Access control lists (ACLs) that restrict SNMP communication to trusted IP addresses are essential—without them, any open device on your network can become an entry point. And one last thing: never leave default community strings like "public" and "private." That's just asking for trouble.
Where SNMP Ends and Real Network Challenges Begin
SNMP is a powerful tool, but it won't solve all your problems - and it's worth realizing this before you convince yourself that "since I have SNMP, everything is under control." The Simple Network Management Protocol has its limitations - it operates over UDP, which means there's no guarantee of packet delivery. Traps may not arrive if the management server has a momentary failure or its buffer is full.
In turn, some devices "lose" SNMP responses if they are too overloaded, which causes false alerts. No SNMP monitoring program can fix this if you don't account for these variables in your alerting policy.
The second issue is that SNMP is not aware of application state. You can have complete statistics from a router and still not know that a VPN service is down. That's why, increasingly, SNMP acts as a foundation but not as the sole source of data. It is combined with active port monitoring, synthetic tests, and sometimes even application-layer analysis. SNMP is not dead—but it's also not sufficient. If you want to know what's really happening with your infrastructure, treat it as one of your tools, not the whole solution. That's when it really works.

































